Database Activity Monitoring – A Security Investment That Pays Off
Smart Data Collective
FEBRUARY 20, 2022
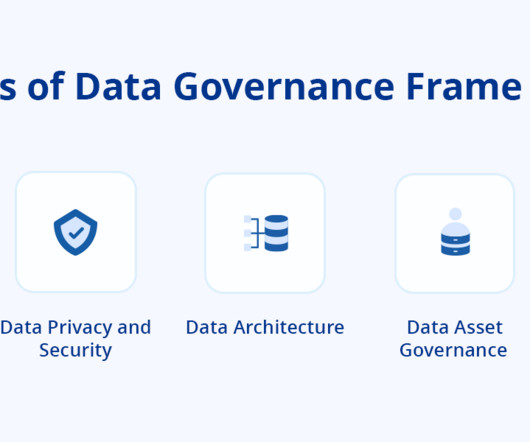
How can database activity monitoring (DAM) tools help avoid these threats? What are the ties between DAM and data loss prevention (DLP) systems? What is the role of machine learning in monitoring database activity? On the other hand, monitoring administrators’ actions is an important task as well.








































Let's personalize your content