5 Considerations for Choosing the Right Data Center
Smart Data Collective
NOVEMBER 20, 2022
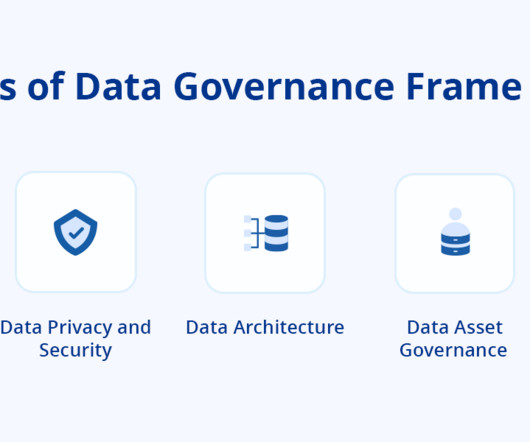
These adaptable solutions can also scale down when the server load decreases, such as during peak and off-peak seasons of a ticket booking system. Even government agencies require special compliance standards to ensure data security, particularly the protection of Personally Identifiable Information (PII). Support and Uptime.






































Let's personalize your content