4 Benefits of Role-Based Access Control (RBAC) and How to Implement It
Dataversity
OCTOBER 16, 2023
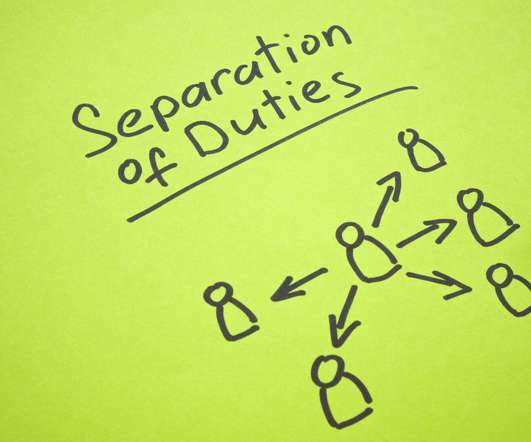
Enter role-based access control (RBAC), a solution that promises to revolutionize how we think about data access and security. As cyber threats evolve, so must our defenses.

















































Let's personalize your content