Why Measuring Cybersecurity Effectiveness Is a Must
Domo
NOVEMBER 1, 2021
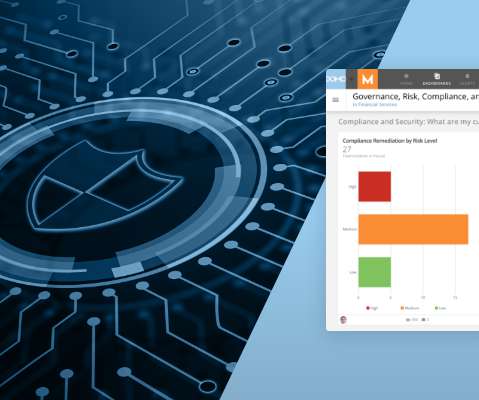
What’s more, often times there is also a disconnect between what a business considers security risks versus what security risks are actually present, creating an inaccurate picture of risk and its potential (or real) impact on the business. Measuring the effectiveness of your cybersecurity program.












Let's personalize your content