5 Tips to Improve the Data Security of Software Applications
Smart Data Collective
JULY 27, 2022
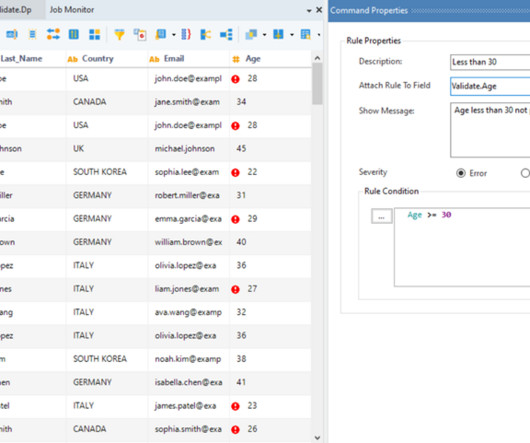
Therefore, the need to protect data from unauthorized access or theft is more important than ever. The of data breaches cannot be overstated. Over 440 million data records were exposed in data breaches in 2018 alone. Hence, it is essential to use a strong password for the data security of the software application.

















Let's personalize your content