Why Measuring Cybersecurity Effectiveness Is a Must
Domo
NOVEMBER 1, 2021
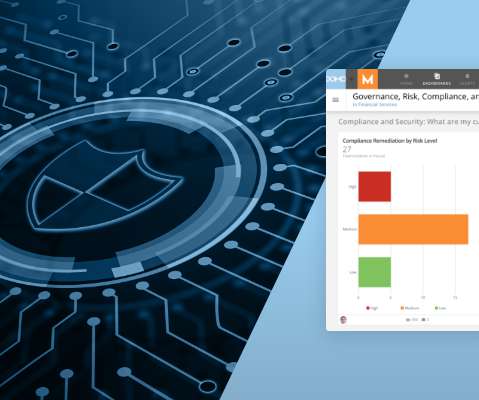
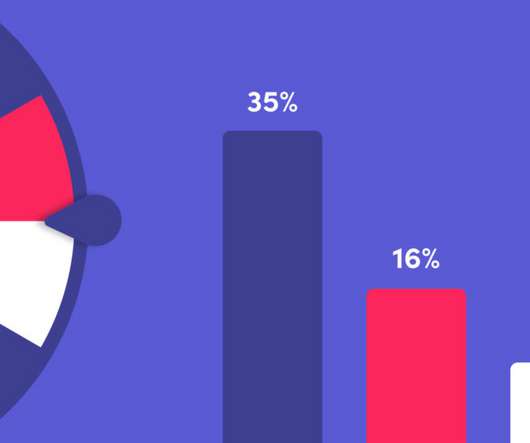
Measuring the effectiveness of your cybersecurity program. Companies have adopted various strategies to measure the effectiveness of their cybersecurity programs. The challenges of measuring cybersecurity effectiveness—and how to conquer them.














Let's personalize your content