12 Cloud Computing Risks & Challenges Businesses Are Facing In These Days
Data Pine
MAY 31, 2022
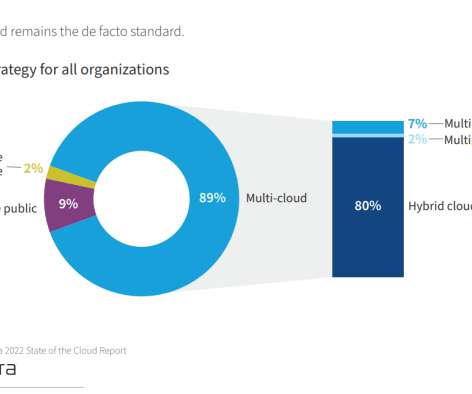
1) What Is Cloud Computing? 2) The Challenges Of Cloud Computing. 3) Cloud Computing Benefits. 4) The Future Of Cloud Computing. Everywhere you turn these days, “the cloud” is being talked about. These challenges of cloud computing are not merely roadblocks to overcome.










Let's personalize your content