Safely Driving Infonomic Growth with Data Access Governance and Security
The Data Administration Newsletter
JULY 5, 2022
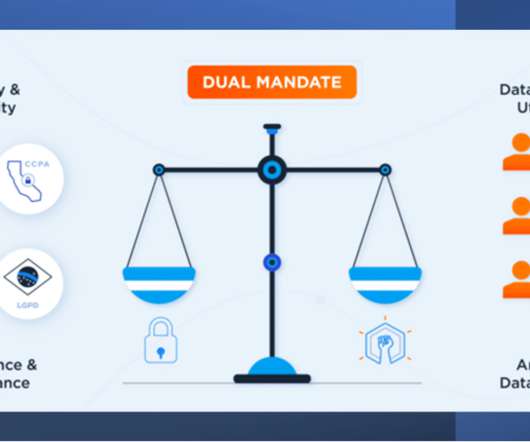
Whichever metaphor you would like to use, what is certain is that no organization will survive the twenty-first century without optimizing the use of its data assets. Similarly, cybersecurity, privacy, and compliance risks increasingly present huge […].








Let's personalize your content