Guarding Your Digital Fortresses: The Imperative of Application Security
In the ever-evolving landscape of cybersecurity, application security stands as the impervious armor that shields your organization’s digital fortresses. Imagine your organization’s applications as the kingdom’s gates – if left unguarded, they become vulnerable entry points for malevolent forces. We understand that as a CIO, CTO, or IT Manager, you take your duty seriously to ensure these gates are fortified.
In order to assist you in this regard, in this blog, we will delve into the realm of application security and shed light on the importance of each layer of defense. We will also explore how a proactive approach to application security can save your organization from potential disasters.
Why Application Security is a Concern
In an era marked by rapid digital transformation, applications have become the lifeblood of businesses. They manage sensitive data, perform critical functions, and are often the first line of interaction with customers. However, these very assets can be exploited if not adequately secured.
Just as the strength of a fortress determines its ability to withstand attacks, the security of your applications dictates your organization’s resilience against cyber threats. Data breaches, unauthorized access, and system vulnerabilities have become common adversaries in today’s digital age.
Picture this: By 2023, ransomware attacks had hit an astonishing 72% of businesses worldwide, marking a significant rise over the past five years and setting a record high. This emphasizes why application security must be at the forefront of your defense strategy.
The consequences of such breaches are dire, leading to financial losses, reputational damage, and regulatory penalties. According to studies, in 2023, data breaches cost companies worldwide an average of USD 4.45 million, showing a worrying 15% increase in just three years. This statistic underscores the urgency of investing in robust application security measures. So, how can you be prepared?
The Building Blocks of Application Security
The Foundation: Architecture Choices
Every castle begins with a strong foundation, and the same principle applies to application security. The architecture choices you make at the outset are akin to building a formidable fortress. An ill-conceived architectural design can leave cracks in the walls for attackers to exploit.
Just as an architect meticulously plans the layout of a castle, your development team should consider security measures when designing your applications. A single weak link in your architectural chain can lead to disaster. Empirical data reveals that a significant 50% of vulnerabilities stem from poor architectural decisions.
Investing time and resources in designing secure architecture is a proactive approach that can significantly reduce the likelihood of security breaches down the line.
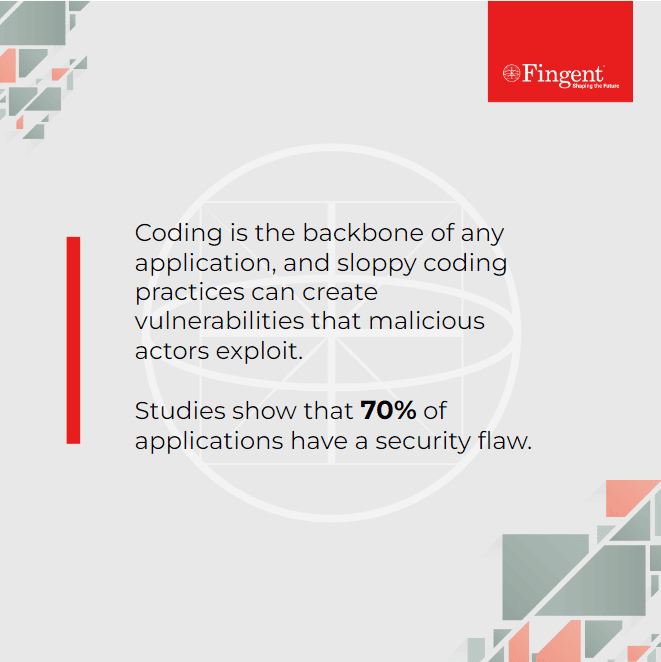
1. Building Strong Walls: Coding Practices and Code Organization
The walls of a fortress serve as the primary defense against intruders. In the world of application security, coding practices and code organization are your virtual walls. Sloppy coding practices create chinks in the armor, allowing malicious code to infiltrate your application.
What can you do?
Imagine coding as the masonry work – each brick (line of code) must be laid meticulously to ensure structural integrity. Security breaches can often result from code vulnerabilities. Ensuring your development team adheres to secure coding practices is akin to reinforcing your fortress walls.
Implementing secure coding practices, conducting regular code reviews, and enforcing coding standards can mitigate vulnerabilities. Training developers in secure coding practices is a crucial step in enhancing your application’s security posture.
2. The Gates and Drawbridges: Library Updates
Just as a castle’s gates and drawbridges are essential entry points, your applications rely on third-party libraries and components. These elements, if left unguarded, can become weak points in your security defenses.
Applications often rely on third-party libraries and components. A concerning fact is that out of about 433,000 websites analyzed, 77% of them use at least one front-end JavaScript library with a known security issue.
Think of libraries as the mechanisms controlling the gates of your fortress. Failing to update them is like leaving the drawbridge down, making it easy for attackers to breach your defenses. Regularly updating these libraries is similar to raising the drawbridge and securing your gates against unwanted visitors.
Additionally, employing automated tools to scan for vulnerabilities in third-party dependencies can help identify and address issues promptly.
3. The Watchful Guards: Application Security Program Management Solutions
Medieval fortresses had vigilant guards patrolling the battlements. Similarly, modern organizations require robust application security program management solutions to keep a watchful eye over their digital assets.
A stark reality: 66% of CIOs are ramping up their investments in cybersecurity. This surge in adoption underscores the growing recognition of the importance of a structured approach to application security.
So, think of these solutions as your digital sentinels, tirelessly scanning for threats and vulnerabilities. These systems serve as your first line of defense, ensuring that potential threats are identified and neutralized promptly.
Read more: A CTO’s Guide To Secured Software Development
How Fingent Helps Fortify Your Digital Kingdom
Without a robust application security strategy in place, your organization is vulnerable to attacks that could have far-reaching consequences.
Just as medieval kings relied on skilled architects, craftsmen, and sentinels to protect their castles, you can depend on Fingent to safeguard your digital kingdom.
At Fingent, we understand the importance of application security, and our expertise in secure architecture design, coding practices, library updates, and application security program management ensures your digital fortresses remain impenetrable. With a deep commitment to security, we offer cutting-edge solutions to protect your digital assets.
In this age of digital warfare, application security is not just an option; it’s your shield against an ever-growing army of cyber threats. Fingent can be your trusted ally in this digital battlefield.
Stay up to date on what's new

Recommended Posts

10 Feb 2024
Why Are Leading Businesses Prioritizing Application Modernization
“In Today’s era of volatility, there is no other way but to re-invent. The only sustainable advantage you can have over others is agility, that’s it. Because nothing else is……

15 Oct 2023 B2B
Hyperscaler Cloud Services: The Next Step In Business Cloud Investment!
Companies can save 20% of the total annual cost if they migrate to the cloud. Hyperscaler Cloud Services can enable businesses to experiment, build, innovate, and run any form of……

30 May 2023 B2B
Cloud Application Development: Empowering Your Business In The Digital Era!
“Cloud computing is really a no-brainer for any start-up because it allows you to test your business plan very quickly for little money. Every start-up, or even a division within……

07 Jul 2022 B2B
Shifting From Cybersecurity to Cyber Resilience – How Are They Different From Each Other!
Cyberattacks are hitting the headlines with increasing frequency. Data breaches and attacks are currently inevitable parts of running an organization. Cybercriminals are adept at using phishing, malware, or insider threats……
Featured Blogs
Stay up to date on
what's new