TCS is one of the most sought-after companies by IT professionals owing to its collaborative and supportive culture and worldwide recognition as a global leader in the IT sector. Every year TCS provides diverse job opportunities for applicants in various fields. To nail the opportunity at TCS, applicants must brace up for the most challenging TCS interview questions with strategic preparation and consistent practice. Commonly asked interview questions given below will test your cognitive and communication skills.
About TCS company
Founded in 1968 by Tata Sons, TCS is headquartered in Mumbai, and is one of the top multinational information technology companies globally. It operates in a vast number of locations across 46 countries and was ranked 64th in the Forbes World's Most Innovative Companies ranking in 2015. It is one of the largest Indian companies in terms of market capitalization. In 2021, TCS recorded a market capitalization of $ 200 billion, making it the first Indian company to do so.
Many well-qualified candidates want to land a job at TCS because the latter provides a vast number of employee benefits, including health insurance, taking a sabbatical, and an environment for learning the right kind of skills while balancing their personal and professional lives. Here are the key stats about TCS:
- Generated revenue of more than $ 26 billion in 2022.
- Raised a net income of $ 5 billion in 2022 and has an operating income of $ 6.8 billion as of 2022.
- Employed more than 528,748 people as of Dec 2021.
TCS Recruitment Process
Written Exam
The time allotted for the written test is 60 minutes, and it consists of four sections - Quantitative Aptitude, Programming Language Efficiency, Coding Test, and E-mail Writing.
Technical Interview
Basic questions based on the resume, branch of specialization, and professional skills are asked, along with a few trickier ones.
Managerial Interview
The TCS interview questions asked in this round depend on the interviewer and range from general technical and HR questions to puzzle questions to gauge your reaction.
HR Interview
It is the final round of the recruitment process. Apart from the usual HR interview questions like strengths and weaknesses, hobbies and background, etc. Questions on work experience and educational background can be expected.
Academic Criteria
Eligible candidates need to have a minimum of 60% result throughout their degree with no backlog. A gap of two years in the career is permissible provided a valid explanation.
TCS Technical Interview Questions
1. Define socket programming and mention the benefits and drawbacks of java sockets.
Socket programming is a type of programming that allows for communication between two devices. This type of communication is often done over a network, such as the Internet. Socket programming can be used to create a variety of applications, such as web servers, chat clients, and more.
Socket programming is a way of using the internet to connect two or more devices. This can be done through a wired connection, such as an Ethernet cable, or a wireless connection, such as Wi-Fi.
Benefits of Java Sockets:
Java Sockets are used in order to allow two applications to communicate over the internet. In simple terms, they provide the ability to connect two devices and allow them to communicate with each other. There are many benefits to using Java Sockets which include: the ability to build network applications quickly, the fact that they are platform independent, and they provide a high level of security. This paper will explore each of these benefits in more depth.
While Java sockets are not the only type of socket available to a developer, they are by far the most commonly used. The biggest reason for this is that they offer a high level of abstraction. This means that a programmer does not have to worry about the underlying communications protocol. Another advantage of using Java sockets is that they allow for the creation of reusable components.
Drawbacks of Java Sockets:
Java sockets, like any other network protocol, have their disadvantages. For example, Java sockets are slower than other protocols because of their use of UDP. Java sockets are a useful way to send data between applications and servers, but there are some drawbacks. First, communication can be slow because Java uses TCP instead of UDP. Additionally, Java does not support synchronous communication, so data can be lost if the two applications are not responding to each other.
2. Define IPsec and mention its components.
IPsec is a security protocol that uses cryptographic security services to protect communications over an Internet Protocol (IP) network. IPsec uses two components to provide security: Authentication Header (AH) and Encapsulating Security Payload (ESP). AH authenticates the sender and the receiver of the data, whereas ESP encrypts the data to protect it from being read by unauthorized users.
IPsec is a protocol that provides authentication and encryption for Internet Protocol communications. It supports network-level peer authentication, data integrity, data confidentiality (encryption), and replay protection. IPsec supports transport and tunnel modes and is mandatory to implement for all IP implementations.
IPsec is a network layer protocol that provides data confidentiality, data integrity, data origin authentication, and data anti-replay service. IPsec uses cryptographic security services to protect communication over untrusted networks such as the Internet. The cryptographic algorithms and protocols used by IPsec have been designed to provide the following security services:
Confidentiality: This service ensures that data cannot be read by anyone other than authorized receivers.
Data integrity: This service ensures that transmitted data has not been altered in any way.
3. What do you mean by subnet mask?
The subnet mask tells the computer which part of the IP address is the network part and which part is the host part. The subnet mask is used to determine whether a given IP address is on the same network as the computer that is requesting the information. If the computer requesting the information has the same subnet mask as the computer that has the information, then the computer requesting the information can assume that the information is on the same network.
Subnetting is the process of dividing a network into smaller subnets, each with its own unique IP address and subnet mask. Subnetting allows you to better control traffic flow and conserve IP addresses. It also allows you to segment your network into different security zones. For example, you could create a separate subnet for your DMZ (Demilitarized Zone) and another subnet for your internal network.
4. Define NAT.
NAT stands for Network Address Translation. When a computer is connected to the internet, the computer’s network card needs to know how to talk to the other computers on the internet. This is done by translating the computer’s public IP address (which is easy to remember, like www.google.com) into the addresses that the internet uses (like 192.168.1.1). NAT is necessary because there are so many different networks in the world and every one of them uses a different IP address.
5. What do you understand by piggybacking?
Piggybacking is when you use someone else’s content to support your own argument. For example, if you’re debating an issue and you use a statistic that your opponent has used in a previous argument, you’re piggybacking. The problem with piggybacking is that it can be unfair. If your opponent is using a statistic that you don’t know about, you might not be able to refute it.
Piggybacking is a way to get benefits from services you use without actually having to use their provider. For example, if you use Gmail, you can piggyback on their email storage so that your email stays in Gmail instead of being sent to your personal email account.
6. What is database schema and its types?
A database schema is the layout of a database, and it includes the organization of data and the relationships between them. There are three main types of schema: physical, logical, and view. A physical schema is the actual database layout, while a logical schema is a representation of the data in the database. A view schema is a subset of the database that is used for a specific purpose.
A database schema is the structure or format of a database. There are three main types of schema: relational, object-oriented, and XML. A relational schema is a table that lists the fields in a database and the relationships between them. An object-oriented schema is a diagram that shows the objects in a database and the relationships between them.
7. Differentiate clustered and non-clustered indexes.
Clustered indexes are great for making sure your data is quickly and easily found, while non-clustered indexes can be more efficient if you only need to look up a single record.
8. What is round trip time?
Round trip time is the time it takes for a data packet to make a round trip from the source to the destination and back. Round trip time is an important metric in computer networking because it can be used as a measure of network latency.
The round-trip time is measured by sending a packet, waiting for its return, and then repeating the process.
9. What is Ping?
Ping is a network traffic measurement tool that is used to diagnose issues with a network. It is a network tool that can be used to check whether a device is reachable. When you ping a device, you send a packet of data to it and wait for a response. If the device is not responding, it might be down or it might be busy. When you ping a device, you can use the ping command to check whether the network is working and whether the device is reachable.
10. List some points about SLIP.
SLIP is a computer protocol used in point-to-point serial connections. It stands for Serial Line Internet Protocol. It was once commonly used to connect personal computers via telephone lines using a modem but has been largely replaced by newer protocols such as PPP. SLIP was defined in RFC 1055.
11. What do you understand about Ethernet?
Ethernet is a computer networking technology standard for Local Area Networks (LANs). It was originally developed in the 1970s by Bob Metcalfe and others working at Xerox PARC. Ethernet uses a bus or star topology and supports data transfer rates of 10 Mbit/s, 100 Mbit/s, 1 Gbit/s, and 10 Gbit/s. Ethernet is standardized by IEEE 802.3. It has largely replaced competing wired LAN technologies such as token rings and FDDI.
Ethernet is one of the most common computer networking technologies in use today. It is a local area network (LAN) technology that provides a way to connect computers and other devices in a limited geographical area. Ethernet uses a special kind of cable and connectors, and it operates at a much higher speed than other LAN technologies.
12. What do you mean by tunnel mode in networking?
Networks are important for allowing data to flow between two or more devices. Tunnel mode in networking allows for more efficient use of networks by breaking data into smaller packets and sending them through a tunnel.
13. Write about the RSA algorithm in brief.
RSA is a calculation for public-key cryptography that is generally utilized in electronic business. It was created in 1977 by Ron Rivest, Adi Shamir, and Len Adleman. The calculation depends on the way that it is truly challenging to factor a huge number that is the result of two indivisible numbers. RSA is utilized in a wide assortment of utilizations, including email, record sharing, and secure correspondence.
14. What is cyclomatic complexity in a software program?
Cyclomatic complexity is a measure of the number of lines of code in a program. The higher the cyclomatic complexity, the more complex the program. Software with high cyclomatic complexity is harder to read and maintain.RSA is an algorithm for public-key cryptography that is widely used in electronic commerce. RSA was created in 1977 by Ron Rivest, Adi Shamir, and Len Adleman. The algorithm is based on the fact that it is very difficult to factor a large number that is the product of two prime numbers. Give an example of a time when you didn't find a bug in black box testing but discovered it in white box testing.
15. Give an example of a time when you didn’t find a bug in Black Box testing but discovered it in white box testing.
Black box testing is a method of testing software where the internal structure of the code being tested is not known. In this type of testing, the tester is only concerned with the inputs and outputs of the system under test. Black box testing is also known as behavioral testing. White box testing, on the other hand, is a method of testing software where the internal structure of the code being tested is known.
16. What is slice splicing in software testing? What are its two types?
Slice splicing is a type of black box testing where the tester only has access to the inputs and outputs of the system under test. There are two types of slice splicing: full and partial. Full slice splicing gives the tester complete access to all inputs and outputs, while partial slice splicing only gives the tester access to a subset of inputs and outputs. I remember a time when I was doing black box testing and I didn't find a bug.
17. Differentiate between AWT and Swing in java.
AWT (Abstract Windowing Toolkit) is a Java GUI toolkit that provides a set of interfaces that allow developers to create user interfaces. Swing is another Java GUI toolkit that provides a more user-friendly interface and is popular among developers who are new to Java. As you can see, AWT is more traditional and Swing is more user-friendly. It provides a rich set of features for creating graphical user interfaces (GUIs). Swing is a more recent windowing environment that was developed specifically for the Java platform.
18. Explain memory leak in C++. How can you avoid it?
When programming in C++, programmers have to be careful to avoid memory leaks. A memory leak is when a program allocates memory but does not deallocate it properly, which can lead to the program using more and more memory over time. To avoid memory leaks, programmers should make sure to properly deallocate memory when they are finished using it.
Memory leaks are a common problem in C++ programming. They occur when the memory that has been allocated is not properly deallocated. This can lead to wasted memory and, in some cases, to program crashes. There are several ways to avoid memory leaks.
19. What do you understand by a command-line argument in C?
Command-line arguments are important in C++. They allow programmers to specify which functions to run and how they should be executed. For example, if you type “./myprogram -arg 1”, the program will run and pass the argument “1” to the myprogram function.
When using the command line in C++, programmers need to be aware of the different types of arguments that they can pass to a program. There are three main types of arguments: positional arguments named arguments, and command-line arguments. Positional arguments are the ones that are listed on the command line. They are the ones you type in sequentially.
20. What do you mean by concurrency control?
Concurrency control is important in any application, but it is particularly crucial in C++ programs. When multiple threads are running in parallel, it is important to make sure that the code is written so that it can be executed asynchronously. Doing so allows the program to handle more concurrent requests and avoid Some of the common problems that can occur when multiple threads are running simultaneously.
21. What do you understand about SQL correlated subqueries?
SQL-correlated subqueries can be a powerful tool for exploring data. They allow you to query data that is related to the data you are already querying. This can be useful when you want to find data that is related to a particular column in your table.
22. Define a checkpoint in a database management system, and when it eventuates.
A checkpoint in a database management system is an event that is triggered when the database reaches a certain point in its performance history. In order to prevent the database from becoming unstable, this checkpoint should be performed at least once every six months.
It is an important event that should be planned for and executed as soon as possible. There are a number of reasons why this should happen, and the most important one is to ensure that the data in the database is correct.
23. What are the two integrity rules in a database management system?
In a database management system, two integrity rules must be followed: the ACID rule and the Atomicity rule. The ACID rule states that any change to an object must be made atomically, which means that all the data about the object must be changed at the same time. This ensures that the database remains consistent and reliable.
24. What exactly are macros? What are the benefits and drawbacks?
A macro is a sequence of commands that you group together as a single command to accomplish a task that would otherwise be too difficult or time-consuming. By using a series of commands to automate a task, you can save an incredible amount of time and effort when performing common tasks such as formatting text, or complex tasks such as building charts that contain numerous components. You can use the Macro Recorder to automatically generate macros for common tasks, and edit the recorded macros to fine-tune them for optimum performance. You can also write macros by using Visual Basic for Applications (VBA) code.
Macros can be a helpful tool for automating tasks, but be aware of their drawbacks. For example, macros can increase the workload of your computer because they run as a background task. Additionally, macros can take up a lot of memory, so you may need to keep track of how much space they are using.
25. What is the difference between JDK and JRE?
The Java Development Kit (JDK) is a software development environment for developing Java applications and components. Java is a general-purpose computer programming language that can be used to develop applications for various platforms including desktops, servers, mobile phones, personal digital assistants, embedded systems, game consoles, set-top boxes, and network-attached storage devices. In contrast, the JRE is the runtime environment for Java applications. It contains a Java Virtual Machine (JVM), class libraries, and other supporting files.
TCS Coding Interview Questions and Answers
26. What is the method to swap two numbers without using a third variable?
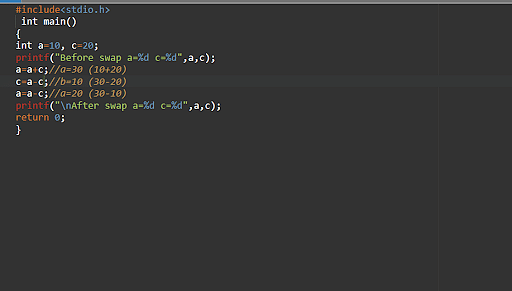
Output -
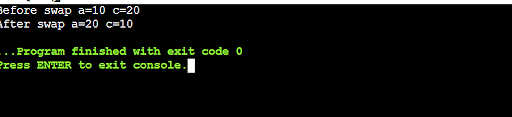
27. Mention the code to reverse a given number using command line arguments.
There are many different ways to reverse a number using the command line arguments. For example, the following code reverses a number using the argv variable: argv[1] - argv[0] . Another way to reverse a number using the command line arguments is using the reversed() function. reversed() takes two arguments: the number to reverse and the string to use as the reverse string.
28. What is meant by cycle stealing?
Cycle stealing is a method of using extra clock cycles to perform other operations that are not related to the main task. In a system with multiple devices, each device may be given a certain number of clock cycles to perform its task. If one device is not using all of its clock cycles, another device can use the extra clock cycles, or 'steal' them.
29. Mention the two concepts of swapping in the context of OS? How does swapping help in better memory management?
Swapping is the process of moving blocks of data from one location to another so that the data can be accessed more easily. Swapping is a common practice in operating systems, particularly when dealing with memory management. Swapping helps to improve memory management by allowing the OS to better utilize the available memory.
There are two concepts of swapping in the context of OS: process swapping and memory swapping. Process swapping allows the operating system to move processes from main memory to disk memory and vice versa. This helps in better memory management as inactive processes can be moved to a disk memory, freeing up space in the main memory. Memory swapping, on the other hand, allows the operating system to move blocks of memory from main memory to disk memory and vice versa.
30. What is the RR Scheduling Algorithm in OS?
The RR Scheduling Algorithm is a scheduling algorithm that is used in operating systems to schedule processes. The algorithm is designed to work with processes that have equal priority. The algorithm works by giving each process a time slice, which is a unit of time that the process is allowed to run. The time slice is usually set to a value that is small enough so that all processes get a fair share of the CPU time.
31. What are interrupts?
Interrupts are a type of signal that can be sent to a process to indicate that an event has occurred. When an interrupt is sent to a process, the process is said to be interrupted. The process can then handle the event that has occurred.
Interrupts are signals that are sent to the CPU by hardware or software devices. These signals tell the CPU to stop what it is doing and start running a different process. Interrupts can be caused by things like a keyboard or mouse being used, or a timer running out. When an interrupt occurs, the CPU saves the state of the current process and starts running the interrupt handler.
32. Explain the functionality of the linked list.
The last node in the list has a link to the first node. Each element in the linked list is connected to the next element in the list. The elements in a linked list are not stored in contiguous memory locations. The linked list can be used to store a sequence of data elements.
Examples:
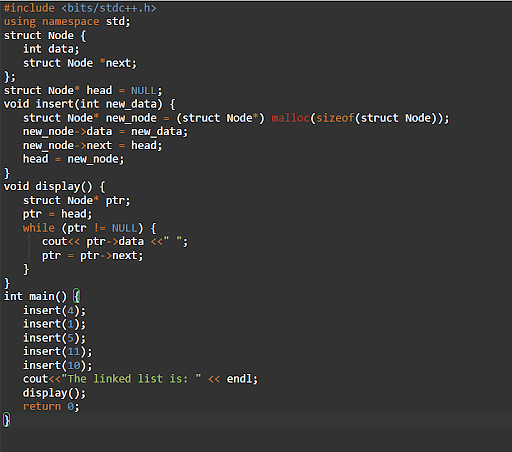
Output:
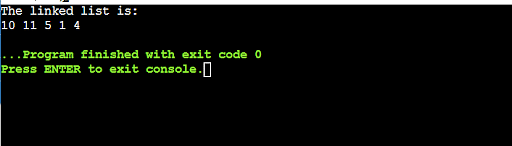
33. Mention the four basic principles of OOPS.
Object Oriented Programming is a great way to develop complex programs. It helps in developing the software by dividing it into objects.
The four basic principles of OOPS are
- Encapsulation:
- Inheritance:
- Polymorphism:
- Abstraction
34. What is inheritance?
Inheritance allows programmers to create new classes that inherit the attributes and methods of existing classes. This can save a lot of time and effort when creating software.
Inheritance is the ability of one class to inherit the attributes and behavior of another class. This is useful for creating hierarchies of classes, where each subclass inherits the attributes and behavior of its superclass. Inheritance is a powerful tool that can be used to create robust and reliable software.
35. What is the method of inheriting the variable of one class to any other class?
Inheritance allows programmers to create new classes that inherit the attributes and methods of existing classes. This can save a lot of time and effort when creating software. Inheritance is a powerful tool that can be used to create robust and reliable software. The behavior of its superclass.
Inheritance can be done in one of two ways: by using the @inherit annotation, or by using the extends keyword. The @inherit annotation is the more common of the two and allows any class to inherit the variables and methods of another class. The extends keyword is less common but allows a class to inherit the variables and methods of another class, as well as the class itself. Inheritance is a powerful tool that can be used to create robust and reliable software.
36. What is polymorphism?
Polymorphism is the ability of a class to behave differently depending on what type of object it is cast to. This can be useful when writing software, as it allows different types of objects to be handled in the same way. For example, a programmer might want to allow a user to input text in either a text box or a text area field. By using polymorphism, the programmer can write code that handles both types of input correctly.
37. What are the different types of inheritance?
Inheritance is the passing of property, titles, debts, rights, and obligations from one generation to the next.
There are three types of inheritance:
1. Legal inheritance: This type of inheritance is given by law and not by will. It also does not depend on any condition.
2. Testamentary inheritance: This type of inheritance can be given in a will.
3. Intestate succession: The person who dies without a will or testament has their property passed to their family members according to the rules laid out in state law.
38. Differentiate between classes and interfaces.
Classes are a fundamental structure in object-oriented programming. They are similar to interfaces in that they define how a class behaves, but they have some important differences. First, classes define the type of object that they create, while interfaces do not. This means that classes can be used to create objects that do not exist in the real world, such as interface classes.
39. What is the software development life cycle?
The software development life cycle (SDLC) is a framework that provides a structure for understanding the steps that are required to develop a piece of software. It is also used as a way to measure the progress of a software development project. The SDLC can be used in different ways, but it is typically divided into six different phases: requirements gathering, design, implementation, testing, deployment, and maintenance. The first step in the SDLC is requirements gathering.
40. Define the normalization of databases, joins, and keys.
Database normalization is a data design technique used to organize a database into tables and columns. The main idea of normalization is to split up your data into multiple tables and to define relationships between them. This process of normalization usually results in a more efficient and effective database design. Normalization is often used when designing relational databases.
In order to maintain data consistency and reduce redundancy, databases are normalized. This involves breaking down tables into their smallest components and only storing related data in a single table. Redundancy can lead to inconsistency, for example, if an address is stored in more than one place and one copy is updated but the other is not. Normalization also involves using keys, which are unique identifiers for each record, and joins, which are used to relate data in different tables.
41. What are loops?
Loops are used to repeat a block of code a given number of times or until a certain condition is met. The most common type of loop is the for loop, which is used to iterate over a sequence of values. For example, a for loop can be used to print each element in a list. Other types of loops include the while loop, which executes a block of code as long as a condition is true, and the do-while loop, which executes a block of code at least once before checking the condition.
In computer programming, a loop is a sequence of instructions that is continually repeated until a certain condition is reached. For example, a programmer might use a loop to check each character in a string to see if it is a letter or a number. Loops are often used when a program needs to repeat an action a set number of times. In some programming languages, the programmer can set the number of times the loop will run.
42. Explain Joins, Views, Normalization, and Triggers.
Joins are used to combine tables into a single table. Views allow you to see the data in two or more tables at the same time. Normalization is the process of making data in a table consistent so that it is easy to understand and use. Triggers are used to automatically run a series of commands when a certain condition is met.
Joins, views, normalization, and triggers are all important when it comes to database design. Joins allow two tables to be combined into a single table, views allow a database user to see data from one table in a different table, normalization makes sure data is formatted correctly, and triggers allow a program to take specific actions when a particular event occurs.
43. List different advantages of DBMS.
The advantages of DBMS are -
- DBMSs are designed to be fault-tolerant, which means that if a hardware or software failure occurs, it can continue working without any data loss.
- DBMSs are designed to be scalable and can grow with the size and complexity of the organization.
- DBMSs provide a standard way of accessing data across all applications, which is important for organizations that need to share data among different departments or systems.
- DBMSs provide an easy way of managing changes in storage capacity by adding more disks or replacing disks with larger ones without disrupting the operation of other parts of the system.
44. What is a Database Management System?
A database management system (DBMS) is a software system that provides an organized structure for storing, retrieving, and manipulating data. DBMSs can be found in a variety of applications, including business, scientific, and engineering fields. DBMSs are essential for managing large sets of data.
45. What are conditional statements?
Conditional statements are extensively used in computer programming as it helps programmers to control the sequence of execution of programs based on some given conditions. If the condition evaluates to true, then the corresponding true block code is executed, otherwise, the false block code is executed. The if...else statement is used when we want to execute a certain statement or a block of statements when a specific condition is satisfied; and execute another statement or another block of statements when the condition is not satisfied. In the else block, we can write a default condition.
46. Differentiate between the foreign key and reference key?
A reference key is a column or set of columns in a table that is used to identify the relationship between different entities in a database. A foreign key is a column or set of columns that are used to establish and enforce a link between the data in two tables. In order for a foreign key to be created, it is important that a primary or unique key exists in the table. In SQL, a foreign key can be used to prevent the deletion of data that is referenced by other data in the database.
47. List the differences and similarities between C and C++?
C is a structured programming language developed by Dennis Ritchie in 1972. It was designed to allow programmers to write software that needed to be efficient and portable. C++ was developed by Bjarne Stroustrup in 1979. It is a superset of the C language and provides object-oriented programming features and a different approach to memory allocation.
The major difference between C and C++ is that C++ provides object-oriented features not available in the original version of the language, such as classes, methods, virtual functions, etc.; this allows programmers to create more robust code with data abstraction and encapsulation, which can make it easier to maintain and reuse code; while this increased level of abstraction can make it more difficult for beginners or those who don't have an understanding of these concepts.
48. Mention the structural difference between the bitmap and b-tree index?
A bitmap index is an indexing structure that is used on large tables with many rows. The bitmap index is a table that stores one row for each key in the table. The rows are ordered by the key value, and the column values of each row represent the number of times this key appears in the table. Bitmap indexes are used to quickly find all keys with a given value or range of values.
A B-tree index is an indexing structure that stores data sorted on one or more columns. The data may be stored internally as a B-tree, which can be searched efficiently by scanning from left to right through adjacent nodes at each level until the desired entry is found, or it may be stored as an external file in which case it can be scanned sequentially from beginning to end.
49. Differentiate between socket and session?
A socket is an object that is used to send and receive data across a network. It is a specific instance of an endpoint that is used to facilitate communication between two computers. A socket can be one-way or two-way. A session is communication between two computers.
50. What is an array?
An array is a collection of data that can be accessed by name. It is similar to a list, but arrays have a specific order.
Arrays are a common data structure in programming. They allow you to store a collection of objects in a single location.
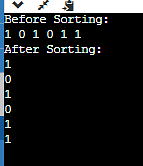
51. If you are given an array of 1s and 0s, how can you arrange the 1s and 0s together in a single array scan? Optimize the boundary conditions.
We can use a two pointer approach for arranging the array in a single array scan. Our goal is to minimize the number of steps needed to scan the entire array in each case.
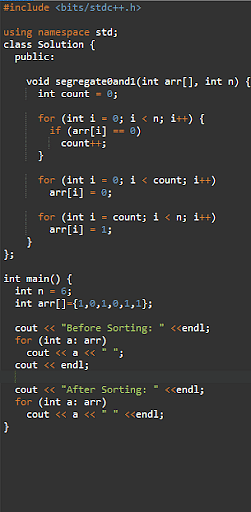
Output -
52. Define data abstraction. What is their importance?
Data abstraction is an important concept in computer science. It is used to hide the details of an implementation from the users of that implementation. Data abstraction is used to create interfaces that are easy to use and understand. It is also used to make code more modular and easier to maintain.
53. Mention a function to swap two numbers without using a temporary variable.
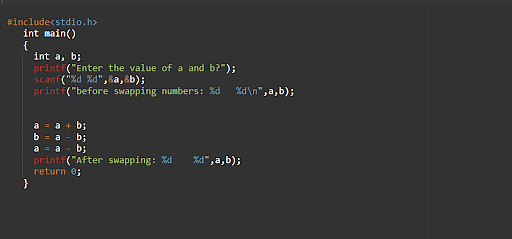
Output -

54. What is memory allocation in C/C++?
Memory allocation is a process by which a computer program requests a certain amount of memory from the operating system. The process of allocating this memory is known as dynamic memory allocation. This article will explain how to allocate memory in C/C++. Allocating memory is important because it allows you to store data that you need to use later on in your program.
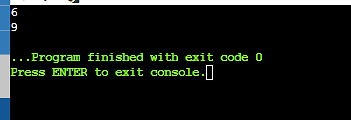
55. Write output of the programme?
Program to print the Nth number in the series.
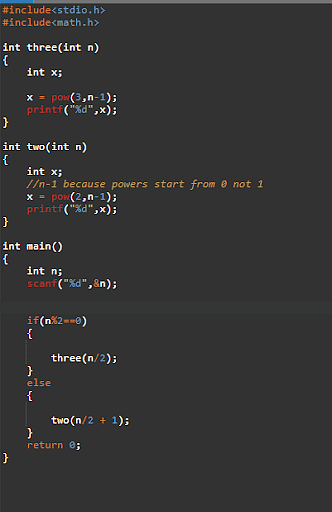
Output-
56. Define virtual function and pure virtual function.
Ans. Virtual functions and pure virtual functions are important aspects of software development. They allow a software developer to abstract away specific details of an algorithm. This abstraction makes the code more readable and maintainable.
virtual functions and pure virtual functions are a type of function. They are called virtual because they do not have a physical location in the program. Instead, they are stored in memory.
57. What are WPF and WCF?
Ans. WPF and WCF are two important technologies used in the .NET Framework. WPF is a platform-independent GUI development framework that was introduced in Windows Vista. WCF is a technology that allows you to create and manage services.
WPF and WCF are two popular frameworks used for building Windows-based software. WPF is a user interface framework, while WCF is a service framework. They both allow developers to create cross-platform applications.
58. Which programming languages are essential to the TCS campus interview?
Important programming languages for the TCS campus interview are:
- C programming
- C++ programming
- Java programming
59. How is C different from C?
C is a superset of C. Major added features in C include Object-Oriented Programming, Exception Handling, and a rich C++ library.
60. Is the C platform independent?
C is a platform-dependent language. This means that programs written in C will only run on the platform for which they were compiled. Platforms can be any combination of hardware and operating system, such as Windows, macOS, Linux, or Android. While C is not strictly portable across all platforms, it is possible to write code that is portable between different platforms.
61. What are structures in C?
Answer: A structure is a user-definable data type in C/C++. It allows you to group certain types of information into a single variable.
62. Explain inheritance in OOPS
Object-oriented programming considers inheritance to be a mechanism based on classes. Inheritance refers to inheriting data members and functions of a parent class to a child class. A class obtained from higher levels is called a child class, and the top-level class from which the child class is obtained is referred to as a sub-class.
63. What four principles does OOPS adhere to?
The four fundamental principles of object-oriented programming systems are abstraction, inheritance, encapsulation, and polymorphism.
64. What prevents Java from being a purely object-oriented language?
Java supports a few of the OOPs ' advanced OOPs properties, including Inheritance, Encapsulation, Polymorphism, Abstraction, and a lot others, but still misses a few of them. Due to this, it's not a pure OOPs language.
65. What distinguishes a clustered index from a non-clustered index?
Clustered index is an index that reorders tables in a way that makes sense for the data. Nonclustered index is an index in which the logical order of the index does not match the physical order of the rows on disk.
66. What does a transparent data management system indicate?
The transparent database management system is a type of database management system (DBMS) that hides its physical structure from users. The physical structure or physical storage structure refers to the memory of a system, and it describes how data is stored on a disk.
67. What do you know about the backbone network?
A backbone network is often a centralized system that distributes different routes and data to multiple networks. It also handles the management of bandwidth on various channels.
TCS Interview Preparation
Answering TCS interview questions confidently requires an intense and strategic prior preparation. The candidates are advised to learn as much as they can about the company to be able to respond suitably to the questions based on the company's requirements. Researching the most expected TCS interview questions and the best answers to those will help answer the challenging questions tactfully. Apart from that, if the candidates need to undergo technical tests, some time should be spent learning these programs to a professional level.
TCS Interview Preparation Tips
- Do your research on the company.
- Develop a practice of explaining your approach and viewpoint to the interviewer.
- Practice the best approach to answer the most expected TCS interview questions.
- Enroll for mock interviews to boost your confidence.
FAQs
1. Does TCS NQT have coding questions?
Yes, TCS NQT has coding questions which you can attempt in any of the five languages given by TCS, including Java, Python, and Pearl.
2. Who is eligible for TCS NQT?
Full-time graduates in B.E., B. TECH., M.E, or M.TECH with 60% throughout academics, including 10th, 12th, UG, and PG courses, are eligible for TCS NQT.
3. What is the salary for freshers in TCS?
According to AmbitionBox, the average salary for freshers in TCS range from ₹1.6 Lakhs to ₹3.6 Lakhs per year.
4. What kind of coding questions are asked in TCS?
The TCS coding section consists of problems on arrays, numbers, sortings, strings, and number systems.
5. What are the basic questions asked in a TCS interview?
Questions regarding your resume, skill set, and educational and family background are some of the basic questions asked in the TCS interview.
6. What is TCS ninja?
It is a job role offered by TCS to fresh recruits, who are mapped to a unit based on their TCS Xplore program performance.
7. How many rounds of interviews are there in TCS?
The TCS recruitment process consists of four rounds that candidates need to clear before moving to the final step.
8. Is the TCS interview tough for experienced?
TCS interview is not easy, but it is not tough to crack for the experienced candidates with the right and strategic preparation.
Conclusion
These TCS interview questions and answers will get you to your dream job. We wish you all the best for your upcoming interviews. If you want to outshine your professional skills then enroll into a Simplilearn's Post Graduate Program in Full Stack Web Development course. Level-up your career with our PGP in Full Stack Web Development course in collaboration with Caltech CTME. This 9-months course covers Agile, JAVA, Hibernate, JPA, Spring Core 50, DevOps and many other software development skills. Kickstart your career, sign-up today and start learning!
If you have any questions or queries, feel free to post them in the comments section below. Our team will get back to you at the earliest.
