Big Data Security: Protecting Your Valuable Assets
Astera
MAY 25, 2023
Big Data Security: Protecting Your Valuable Assets In today’s digital age, we generate an unprecedented amount of data every day through our interactions with various technologies. The sheer volume, velocity, and variety of big data make it difficult to manage and extract meaningful insights from.



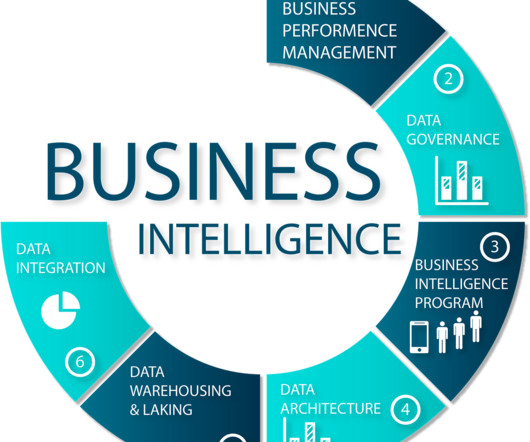



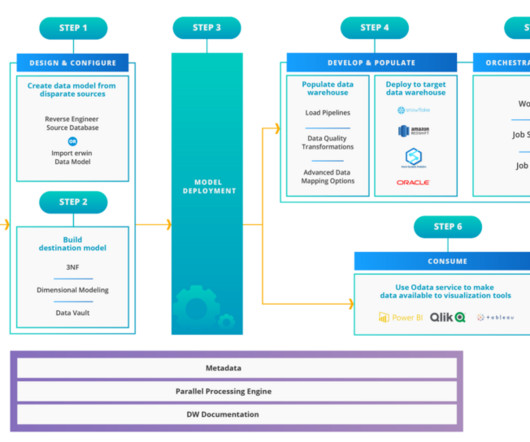














Let's personalize your content